May 18, 2025·8 min
Build a Web App for Company Announcements & Acknowledgements
Learn how to design and build a web app for company-wide announcements, targeted delivery, acknowledgements, reminders, and reporting—step by step.
Learn how to design and build a web app for company-wide announcements, targeted delivery, acknowledgements, reminders, and reporting—step by step.

Company updates don’t fail because people don’t care—they fail because the message gets buried. A policy change arrives in email next to customer threads, an all-hands note is posted in a chat channel that moves too fast, and a safety update is mentioned verbally but never documented. When something is truly important, “we sent it” isn’t the same as “people saw it,” and that gap makes compliance, follow-up, and accountability hard to prove.
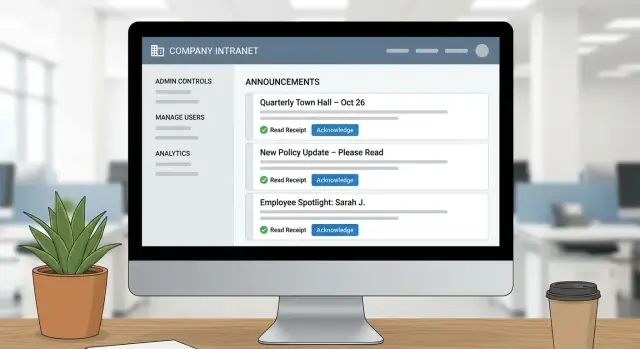
A company announcements app should do more than publish posts. In v1, aim for a simple, reliable announcement workflow that produces evidence:
That combination of read receipts tracking plus acknowledgement evidence becomes your audit trail for acknowledgements, which is often the real business requirement.
Designing for actual stakeholders keeps the product from turning into generic internal communications software:
A focused MVP is easier to ship and easier to adopt. For v1, prioritize the core announcement workflow, role-based access control, notifications, acknowledgements, and basic reporting. Defer complexity that doesn’t prove value yet.
V1 (must-have):
Later (nice-to-have):
If you can clearly state, “This app ensures critical updates are delivered, acknowledged, and provable,” you have a sharp definition of success for the rest of the build.
This kind of app succeeds when it makes important messages hard to miss, easy to understand, and easy to prove they were seen. Start by defining the minimum set of features that support clear publishing, precise targeting, and reliable acknowledgement records.
Each announcement should support a clear structure: title, formatted body, and attachments (PDFs, images, policies). Add publish windows (start/end) so posts can be scheduled and automatically expire, plus urgency levels (e.g., Normal, Important, Critical) that affect how prominently the item appears.
A practical requirement: authors need to fix typos without breaking trust, while admins need the ability to withdraw an announcement (with a visible “withdrawn” state) when information changes.
Targeting is what turns an announcement tool into usable internal communications software. Support common scopes out of the box:
Users should only see what applies to them, but admins should be able to preview how an announcement looks for different audiences.
Not every post needs a read receipt. Make acknowledgements configurable per announcement:
The system should clearly show “Acknowledged / Not acknowledged / Overdue” at both the individual and aggregate level.
Admins typically need templates for recurring posts (policy updates, IT maintenance), approvals for sensitive announcements, and scheduling. Treat these as first-class requirements early—retro-fitting approvals later can disrupt the workflow and data model.
A clear workflow prevents announcements from becoming “just another post” and makes acknowledgement reporting trustworthy. Start by mapping the end-to-end path for each role, then define the states an announcement can be in.
Most teams benefit from a simple, explicit lifecycle:
Treat Read as a passive event (opened/viewed) and Acknowledged as an explicit action (clicked “I understand” or completed a required prompt). This avoids confusion when someone opens a notification but doesn’t commit to compliance.
For company policy and audit needs, acknowledgements should almost always be per user, not per device or session. A per-session “read receipt” can be useful for UX (e.g., don’t show the same banner twice in a day), but it shouldn’t replace the user-level record.
Late acknowledgements and HR events can break reports if you don’t define rules:
With these journeys documented, you can design screens and APIs that match real behavior instead of assumptions.
Access control is where an announcements app becomes trustworthy. People need to know only the right users can publish to the whole company, and that acknowledgement reports aren’t visible to everyone.
For most mid-sized and large companies, start with Single Sign-On (SSO) using SAML or OIDC. It reduces password support tickets, makes offboarding safer (disable the corporate account once), and often enables conditional access (like requiring MFA on untrusted devices).
If you’re building for small teams or an early MVP, email/password can be acceptable—just make it optional, and design your system so you can add SSO later without rewriting user identities. A common approach is to store users by a stable internal ID, and attach one or more “login methods” (password, OIDC provider, etc.).
Define roles that match how announcements actually move through your organization:
Beyond roles, document key permissions explicitly:
Groups can be synced from your HR directory (best for accuracy) or managed manually (faster to ship). If you sync, support attributes like department, location, and manager. If you manage manually, add clear ownership (who can edit a group) and change history so targeting decisions are auditable later.
A clear data model makes the rest of the app easier: publishing flows become predictable, reporting becomes trustworthy, and you can prove who saw what (and when) without messy spreadsheets.
Start with an announcements table that holds the content and lifecycle state:
id, title, body (or body_html)status: draft, published, archivedcreated_at, updated_at, plus published_at and archived_atcreated_by, published_byKeep “draft vs published” strict. A draft should never generate notifications or acknowledgements.
Avoid encoding audience logic only in code. Model it:
groups (e.g., “Warehouse”, “Managers”)group_members (group_id, user_id, validity dates if needed)audience_rules if you support filters like location/departmentFor reporting, create a materialized announcement_recipients table (the “recipients list”) generated at publish time:
announcement_id, user_id, source (group/rule/manual)recipient_created_atThis snapshot prevents reports from changing later when someone switches departments.
Use an acknowledgements table:
announcement_id, user_idstatus (e.g., pending, acknowledged)acknowledged_atnoteAdd a unique constraint on (announcement_id, user_id) to stop duplicates.
Store file metadata in the database, and the actual blobs in object storage:
attachments: id, announcement_id, file_name, content_type, size, storage_key, uploaded_atThis keeps your database lean while supporting large PDFs and images without performance issues.
Your backend is the source of truth for announcements, who can see them, and who has acknowledged them. Keep it boring and predictable: clear endpoints, consistent responses, and strict permission checks.
Start with a small set of API actions that map to what admins and employees actually do:
A simple shape might look like:
GET /api/announcements (feed)POST /api/announcements (create)GET /api/announcements/{id} (details)PATCH /api/announcements/{id} (edit)POST /api/announcements/{id}/publishPOST /api/announcements/{id}/acknowledgementsAnnouncement lists grow quickly, so make pagination a default. Add filters that match real admin questions and employee needs:
Use consistent query parameters (e.g., ?page=2&pageSize=20&team=Sales&status=published&from=2025-01-01).
If you need instant “new announcement” banners, consider WebSockets or Server-Sent Events. If not, simple polling (e.g., refresh every 60–120 seconds) is easier to operate and usually good enough.
Acknowledgements should be idempotent: submitting twice shouldn’t create two records.
Implement one of these approaches:
(announcement_id, user_id) and treat duplicates as success.Idempotency-Key header per submission for extra safety on flaky networks.This keeps reporting accurate and avoids confusing “double acknowledged” audit entries.
An announcements app only works if employees can skim it quickly, trust what they see, and complete acknowledgements without friction. Prioritize clarity over “cool” UI—most users will open it between meetings on a laptop or phone.
Design the feed so the most important items stand out immediately:
Keep the “unread” state obvious but not noisy. A simple badge and bold title usually beats heavy banners.
On the detail page, put the essentials above the fold:
If the acknowledgement includes a policy statement, show it right next to the button (not hidden behind another click). After acknowledging, replace the CTA with a confirmation and timestamp so users feel confident it went through.
Build for real-world usage: full keyboard navigation, visible focus states, readable typography, and sufficient contrast. Don’t rely on color alone to indicate priority or status; pair it with icons and text.
Admins need a workflow-focused interface: drafts, an approval queue, scheduling, and an audience preview that answers “Who will actually see this?” before publishing. Include a quick “view as employee” mode so admins can verify formatting and attachments without guessing.
Notifications are what turn “announcement posted” into “announcement read and acknowledged.” The goal is simple: reach people on the channels they actually check, without spamming them.
Start with in-app notifications as the source of truth, then add delivery channels based on your workforce:
Let admins choose per announcement which channels to use, and let employees set personal preferences (where policy allows).
Tie reminders to an acknowledgement due date:
Keep the logic transparent: show the planned reminder schedule in the announcement composer so publishers know what will be sent.
Respect “do not disturb” windows. Store each user’s time zone and apply quiet hours locally (e.g., 20:00–08:00). If a reminder falls inside quiet hours, queue it for the next allowed window.
Email won’t always land. Capture provider events (delivered, bounced, blocked) and surface a simple status like “Delivered” or “Failed” to admins. For repeated bounces or invalid emails, auto-suppress that address and prompt an update rather than retrying endlessly.
Announcements are only useful when you can prove they were seen and understood. A good acknowledgement system turns “we posted it” into “we can demonstrate who confirmed it, and when.”
Not every message needs the same level of certainty. Support a few acknowledgement modes so admins can pick what fits:
Keep the UI clear: show the acknowledgement requirement and deadline right next to the announcement, not buried on a separate page.
For audits and internal investigations, you need an append-only record. Store acknowledgement events as immutable entries containing:
Avoid “updating” acknowledgement rows in place. Instead, append new events and compute the current status from the latest valid event.
If an announcement changes meaningfully, prior acknowledgements shouldn’t automatically carry over. Version your announcement content and mark a new version as requires re-acknowledgement. Then:
Admins and auditors often need evidence outside the app. Provide:
Security for an announcements and acknowledgements app isn’t only about preventing breaches. It’s also about making sure the right people can see the right messages, proving what happened later, and keeping data only as long as you truly need it.
Start with the basics that reduce risk without making the product harder to use:
Even “internal” apps get abused—sometimes accidentally. Add rate limiting to endpoints that can be spammed (sign-in, search, acknowledgement submission). If you expose any public-facing endpoints (like SSO callbacks or webhook receivers), protect them with:
Attachments are a common weak spot. Treat them like untrusted input:
Acknowledgements can reveal employment details (who read what, when). Decide upfront:
If your organization has compliance requirements (SOC 2, ISO 27001, GDPR, HIPAA), document how access is controlled, how logs are protected, and how data retention is enforced—then implement those controls consistently.
Integrations are what turn a “nice portal” into something employees actually notice. The goal is simple: meet people where they already work, and remove manual admin steps that slow adoption.
A common pattern is: publish an announcement in your app, then automatically post a notification to the right channel(s) with a deep link back to the announcement.
Keep the chat message short and actionable: title, who it applies to, and one link to “Read & acknowledge.” Avoid dumping the full text into chat—people will skim and forget.
If your company uses an HRIS (e.g., Workday, BambooHR, HiBob), syncing the employee directory saves hours and reduces errors. Start with basics:
Even a daily sync is often enough for MVP; real-time sync can come later.
Webhooks let other systems react instantly when something happens. Useful events include:
announcement.publishedannouncement.acknowledgedannouncement.overdueThese can trigger workflows in tools like Zapier/Make or internal scripts—for example, creating a ticket when overdue acknowledgements cross a threshold.
Early on, you may not have directory integrations ready. Provide CSV import/export for users and groups so admins can start quickly, then transition to sync later.
For more rollout tips, see /blog/employee-comms-checklist. If you’re packaging this as a product, explain integrations clearly on /pricing so buyers can confirm fit fast.
Shipping an announcements app isn’t just “push to production.” Day-to-day success depends on predictable deployments, background processing that doesn’t block users, and quick visibility when something breaks.
If you want to move from spec to a working MVP quickly, a vibe-coding platform like Koder.ai can help you stand up the core workflow (React frontend, Go backend, PostgreSQL) from a structured chat prompt—then iterate using planning mode, snapshots, and rollback as you refine targeting, notifications, and acknowledgement reporting. When you’re ready, you can export the source code and deploy/host with custom domains.
Plan for three environments: dev, staging, and prod. Staging should mirror production as closely as possible (same database engine, similar email provider, same file storage type) so you catch issues before employees do.
Keep configuration outside the codebase using environment variables (or a secrets manager). Typical config items include email/SMS credentials, base URL, database connection strings, file storage keys, and feature flags (e.g., “require acknowledgement” on/off).
Even for an MVP, some tasks shouldn’t run in the web request:
Use a job queue and make jobs idempotent (safe to run twice) so retries don’t spam people.
Set up monitoring on day one:
Also log key events like “announcement published,” “reminder sent,” and “acknowledged,” so support can answer questions without guessing.
MVP: deploy via CI/CD, staging approval step, database migrations, admin user bootstrap, daily backups, basic monitoring, and a manual “resend reminder” tool.
V2 ideas: self-serve analytics dashboards, advanced scheduling (time zones, quiet hours), templated announcement types, and automated escalation (notify a manager if overdue).
In most companies, the real requirement isn’t “posting updates”—it’s proving delivery and follow-up. A good v1 should:
Keep the lifecycle explicit so reporting is trustworthy:
Treat Read as a passive event (opened/viewed) and Acknowledged as an explicit action (“I understand”). Use read events for UX (e.g., unread badges), but use acknowledgements for compliance and audit.
If you only track reads, you’ll struggle to prove policy confirmation or completion by a due date.
In most cases, make acknowledgements per user, not per device or session. Per-user records map to HR/compliance needs and avoid loopholes (e.g., someone acknowledging on a shared kiosk).
You can still use session-level “seen” flags for UI (like not showing the same banner repeatedly), but don’t treat those as evidence.
Ship targeting that matches how orgs actually operate:
Also add an admin “preview as audience” view so publishers can confirm exactly who will receive it before hitting publish.
Create a recipient snapshot at publish time (e.g., an announcement_recipients table). That way, reports don’t change later when someone changes department or location.
This is essential for auditability: the app can answer “who was targeted when it was published?” even months later.
Make acknowledgement submission idempotent so retries don’t create duplicates:
(announcement_id, user_id) and treat duplicates as success, and/orIdempotency-Key for flaky networksThis keeps audit trails clean and prevents confusing “double acknowledged” states.
Pick channels based on your workforce and keep reminders tied to due dates:
Show the planned reminder schedule in the composer so publishers know what will be sent.
Version announcements and require re-acknowledgement for material changes:
Avoid silently editing published content without trace—trust and compliance both suffer.
Store an append-only log of publishing and acknowledgement events that includes:
Then provide CSV exports and a printable summary view for auditors/managers. For rollout guidance, you can also reference /blog/employee-comms-checklist.