Sep 05, 2025·8 min
Building a Web App for Compliance Management & Audit Trails
A practical blueprint for building a compliance web app with reliable audit trails: requirements, data model, logging, access control, retention, and reporting.
A practical blueprint for building a compliance web app with reliable audit trails: requirements, data model, logging, access control, retention, and reporting.

Building a compliance management web application is less about “screens and forms” and more about making audits repeatable. The product succeeds when it helps you prove intent, authority, and traceability—quickly, consistently, and without manual reconciliation.
Before you pick a database or sketch screens, write down what “compliance management” actually means in your organization. For some teams, it’s a structured way to track controls and evidence; for others, it’s primarily a workflow engine for approvals, exceptions, and periodic reviews. The definition matters because it determines what you must prove during an audit—and what your app must make easy.
A useful starting statement is:
“We need to show who did what, when, why, and under whose authority—and retrieve proof quickly.”
That keeps the project focused on outcomes, not features.
List the people who will touch the system and the decisions they make:
Document the “happy path” and the common detours:
For a compliance web application, v1 success is usually:
Keep v1 narrow: roles, basic workflows, audit trail, and reporting. Push “nice-to-haves” (advanced analytics, custom dashboards, broad integrations) to later releases once auditors and control owners confirm the fundamentals work.
Compliance work goes sideways when regulations stay abstract. The goal of this step is to turn “be compliant with SOC 2 / ISO 27001 / SOX / HIPAA / GDPR” into a clear backlog of features your app must provide—and evidence it must produce.
List the frameworks that matter for your organization and why. SOC 2 might be driven by customer questionnaires, ISO 27001 by a certification plan, SOX by finance reporting, HIPAA by handling PHI, and GDPR by EU users.
Then define boundaries: which products, environments, business units, and data types are in-scope. This prevents building controls for systems the auditors won’t even look at.
For each framework requirement, write the “app requirement” in plain language. Common translations include:
A practical technique is to create a mapping table in your requirements doc:
Framework control → app feature → data captured → report/export that proves it
Auditors usually ask for “complete change history,” but you must define it precisely. Decide which events are audit-relevant (e.g., login, permission changes, control edits, evidence uploads, approvals, exports, retention actions) and the minimum fields each event must record.
Also document retention expectations per event type. For example, access changes may require longer retention than routine view events, while GDPR considerations may limit retaining personal data longer than necessary.
Treat evidence as a first-class product requirement, not an attachment feature bolted on later. Specify what evidence must support each control: screenshots, ticket links, exported reports, signed approvals, and files.
Define metadata you need for auditability—who uploaded it, what it supports, versioning, timestamps, and whether it was reviewed and accepted.
Schedule a short working session with internal audit or your external auditor to confirm expectations: what “good” looks like, what sampling will be used, and which reports they expect.
This upfront alignment can save months of rework—and helps you build only what actually supports an audit.
A compliance app lives or dies by its data model. If controls, evidence, and reviews aren’t clearly structured, reporting becomes painful and audits turn into screenshot hunts.
Start with a small set of well-defined tables/collections:
Model relationships explicitly so you can answer “show me how you know this control works” in one query:
Use stable, human-readable IDs for key records (e.g., CTRL-AC-001) alongside internal UUIDs.
Version anything that auditors expect to be immutable over time:
Store attachments in object storage (e.g., S3-compatible) and keep metadata in your database: filename, MIME type, hash, size, uploader, uploaded_at, and retention tag. Evidence can also be a URL reference (ticket, report, wiki page).
Design for the filters auditors and managers will actually use: framework/standard mapping, system/app in scope, control status, frequency, owner, last tested date, next due date, test result, exceptions, and evidence age. This structure makes /reports and exports straightforward later.
An auditor’s first questions are predictable: Who did what, when, and under what authority—and can you prove it? Before you implement logging, define what an “audit event” means in your product so every team (engineering, compliance, support) records the same story.
For each audit event, capture a consistent core set of fields:
Auditors expect clear categories, not free-form messages. At minimum, define event types for:
For important fields, store before and after values so changes are explainable without guessing. Redact or hash sensitive values (e.g., store “changed from X to [REDACTED]”) and focus on fields that affect compliance decisions.
Include request metadata to tie events back to real sessions:
Write this rule down early and enforce it in code reviews:
A simple event shape to align on:
{
"event_type": "permission.change",
"actor_user_id": "u_123",
"target_user_id": "u_456",
"resource": {"type": "user", "id": "u_456"},
"occurred_at": "2026-01-01T12:34:56Z",
"before": {"role": "viewer"},
"after": {"role": "admin"},
"context": {"ip": "203.0.113.10", "user_agent": "...", "session_id": "s_789", "correlation_id": "c_abc"},
"reason": "Granted admin for quarterly access review"
}
An audit log is only useful if people trust it. That means treating it like a write-once record: you can add entries, but you never “fix” old ones. If something was wrong, you log a new event that explains the correction.
Use an append-only audit log table (or an event stream) where each record is immutable. Avoid UPDATE/DELETE on audit rows in application code, and enforce immutability at the database level when possible (permissions, triggers, or using a separate storage system).
Each entry should include: who/what acted, what happened, what object was affected, before/after pointers (or a diff reference), when it happened, and where it came from (request ID, IP/device if relevant).
To make edits detectable, add integrity measures such as:
The goal isn’t crypto for its own sake—it’s to be able to show an auditor that missing or altered events would be obvious.
Log system actions (background jobs, imports, automated approvals, scheduled syncs) distinctly from user actions. Use a clear “actor type” (user/service) and a service identity so “who did it” never becomes ambiguous.
Use UTC timestamps everywhere, and rely on a trustworthy time source (e.g., database timestamps or synchronized servers). Plan for idempotency: assign a unique event key (request ID / idempotency key) so retries don’t create confusing duplicates, while still allowing you to record genuine repeated actions.
Access control is where compliance expectations become day-to-day behavior. If the app makes it easy to do the wrong thing (or hard to prove who did what), audits turn into debates. Aim for simple rules that reflect how your organization actually works, then enforce them consistently.
Use role-based access control (RBAC) to keep permission management understandable: roles like Viewer, Contributor, Control Owner, Approver, and Admin. Give each role only what it needs. For example, a Viewer may read controls and evidence but can’t upload or edit anything.
Avoid “one super-user role” that everyone gets. Instead, add temporary elevation (time-boxed admin) when needed, and make that elevation auditable.
Permissions should be explicit per action—view / create / edit / export / delete / approve—and constrained by scope. Scope can be:
This prevents a common failure mode: someone has the right action, but across too wide an area.
Separation of duties shouldn’t be a policy document—it should be a rule in code.
Examples:
When a rule blocks an action, show a clear message (“You can request this change, but an Approver must sign off.”) so users don’t look for workarounds.
Any change to roles, group membership, permission scopes, or approval chains should generate a prominent audit entry with who/what/when/why. Include the previous and new values, plus the ticket or reason if available.
For high-risk operations (exporting a full evidence set, changing retention settings, granting admin access), require step-up authentication—re-enter password, MFA prompt, or SSO re-auth. It reduces accidental misuse and makes the audit story much stronger.
Retention is where compliance tools often fail in real audits: records exist, but you can’t prove they were kept for the right duration, protected from premature deletion, and disposed of predictably.
Create explicit retention periods per record category, and store the chosen policy alongside each record (so the policy is auditable later). Common buckets include:
Make the policy visible in the UI (e.g., “kept for 7 years after close”) and immutable once the record is finalized.
Legal hold should override every automated purge. Treat it as a state with a clear reason, scope, and timestamps:
If your app supports deletion requests, legal hold must clearly explain why deletion is paused.
Retention is easier to defend when it’s consistent:
Document where backups live, how long they’re kept, and how they’re protected. Schedule restoration tests and record the results (date, dataset, success criteria). Auditors often ask for proof that “we can restore” is more than a promise.
For privacy obligations, define when you delete, when you redact, and what must remain for integrity (e.g., keep an audit event but redact personal fields). Redactions should be logged as changes, with the “why” captured and reviewed.
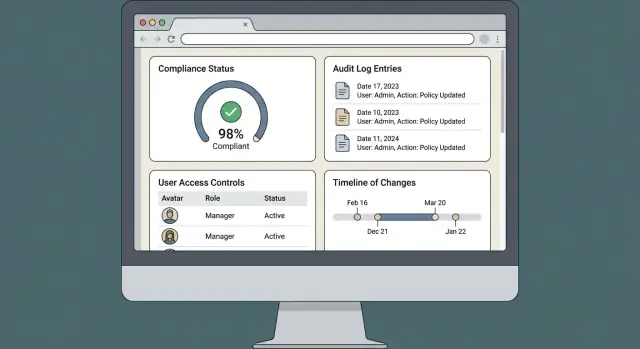
Auditors rarely want a tour of your UI—they want fast answers that can be verified. Your reporting and search features should reduce back-and-forth: “Show me all changes to this control,” “Who approved this exception,” “What’s overdue,” and “How do you know this evidence was reviewed?”
Provide an audit log view that’s easy to filter by user, date/time range, object (control, policy, evidence item, user account), and action (create/update/approve/export/login/permission change). Add free-text search over key fields (e.g., control ID, evidence name, ticket number).
Make filters linkable (copy/paste URL) so an auditor can reference the exact view they used. Consider a “Saved views” feature for common requests like “Access changes last 90 days.”
Create a small set of high-signal compliance reports:
Each report should clearly show definitions (what counts as “complete” or “overdue”) and the as-of timestamp of the dataset.
Support exports to CSV and PDF, but treat exporting as a regulated action. Every export should generate an audit event containing: who exported, when, which report/view, filters used, record count, and file format. If feasible, include a checksum for the exported file.
To keep report data consistent and reproducible, ensure the same filters yield the same results:
For any control, evidence item, or user permission, add an “Explain this record” panel that translates change history into plain language: what changed, who changed it, when, and why (with comment/justification fields). This reduces confusion and prevents audits from turning into guesswork.
Security controls are what make your compliance features believable. If your app can be edited without proper checks—or your data can be read by the wrong person—your audit trail won’t satisfy SOX, GxP expectations, or internal reviewers.
Validate inputs on every endpoint, not just in the UI. Use server-side validation for types, ranges, and allowed values, and reject unknown fields. Pair validation with strong authorization checks on every operation (view, create, update, export). A simple rule: “If it changes compliance data, it must require an explicit permission.”
To reduce broken access control, avoid “security by hiding UI.” Enforce access rules in the backend, including on downloads and API filters (for example, exporting evidence for one control must not leak evidence for another).
Cover the basics consistently:
Use TLS everywhere (including internal service-to-service calls). Encrypt sensitive data at rest (database and backups), and consider field-level encryption for items like API keys or identifiers.
Store secrets in a dedicated secrets manager (not in source control or build logs). Rotate credentials and keys on a schedule, and immediately after staff changes.
Compliance teams value visibility. Create alerts for failed login spikes, repeated 403/404 patterns, privilege changes, new API tokens, and unusual export volume. Make alerts actionable: who, what, when, and the affected objects.
Use rate limiting for login, password reset, and export endpoints. Add account lockout or step-up verification based on risk (e.g., lock after repeated failures, but provide a safe recovery path for legitimate users).
Testing a compliance app isn’t just “does it work?”—it’s “can we prove what happened, who did it, and whether they were allowed to?” Treat audit readiness as a first-class acceptance criterion.
Write automated tests that assert:
CONTROL_UPDATED, EVIDENCE_ATTACHED, APPROVAL_REVOKED).Also test negative cases: failed attempts (permission denied, validation errors) should either create a separate “denied action” event or be intentionally excluded—whatever your policy states—so it’s consistent.
Permissions testing should focus on preventing cross-scope access:
Include API-level tests (not only UI), since auditors often care about the true enforcement point.
Run traceability checks where you start from an outcome (e.g., a control was marked “Effective”) and confirm you can reconstruct:
Audit logs and reports grow quickly. Load test:
Maintain a repeatable checklist (linked in your internal runbook, e.g., /docs/audit-readiness) and generate a sample evidence package that includes: key reports, access listings, change history samples, and log integrity verification steps. This turns audits from a scramble into a routine.
Shipping a compliance web application isn’t just “release and forget.” Operations is where good intentions either become repeatable controls—or turn into gaps you can’t explain during an audit.
Schema and API changes can silently break traceability if they overwrite or reinterpret old records.
Use database migrations as controlled, reviewable change units, and favor additive changes (new columns, new tables, new event types) over destructive ones. When you must change behavior, keep APIs backward-compatible long enough to support older clients and replay/reporting jobs. The goal is simple: historical audit events and evidence must remain readable and consistent across versions.
Maintain clear environment separation (dev/stage/prod) with distinct databases, keys, and access policies. Staging should mirror production enough to validate permission rules, logging, and exports—without copying sensitive production data unless you have explicit, approved sanitization.
Keep deployments controlled and repeatable (CI/CD with approvals). Treat a deployment as an auditable event: record who approved it, what version shipped, and when.
Auditors often ask, “What changed, and who authorized it?” Track deployments, feature-flag flips, permission model changes, and integration configuration updates as first-class audit entries.
A good pattern is an internal “system change” event type:
SYSTEM_CHANGE: {
actor, timestamp, environment, change_type,
version, config_key, old_value_hash, new_value_hash, ticket_id
}
Set up monitoring that’s tied to risk: error rates (especially write failures), latency, queue backlogs (evidence processing, notifications), and storage growth (audit log tables, file buckets). Alert on missing logs, unexpected drops in event volume, and permission-denied spikes that might indicate misconfiguration or abuse.
Document “first hour” steps for suspected data integrity issues or unauthorized access: freeze risky writes, preserve logs, rotate credentials, validate audit log continuity, and capture a timeline. Keep runbooks short, actionable, and linked from your ops docs (for example, /docs/incident-response).
A compliance app isn’t “done” when it ships. Auditors will ask how you keep controls current, how changes are approved, and how users stay aligned with the process. Build governance features into the product so continuous improvement is normal work—not a scramble before an audit.
Treat app and control changes as first-class records. For each change, capture the ticket or request, the approver(s), release notes, and a rollback plan. Connect these directly to the impacted control(s) so an auditor can trace:
why it changed → who approved → what changed → when it went live
If you already use a ticketing system, store references (IDs/URLs) and mirror key metadata in your app to keep evidence consistent even if external tools change.
Avoid editing a control “in place.” Instead, create versions with effective dates and clear diffs (what changed and why). When users submit evidence or complete a review, link it to the specific control version they were responding to.
This prevents a common audit problem: evidence collected under an older requirement appearing to “not match” today’s wording.
Most compliance gaps are process gaps. Add concise in-app guidance where users act:
Track training acknowledgements (who, what module, when) and show just-in-time reminders when a user is assigned a control or review.
Maintain living documentation inside the app (or linked via /help) that covers:
This reduces back-and-forth with auditors and speeds up onboarding for new admins.
Bake governance into recurring tasks:
When these reviews are managed in-app, your “continuous improvement” becomes measurable and easy to demonstrate.
Compliance tools often start as an internal workflow app—and the fastest path to value is a thin, auditable v1 that teams actually use. If you want to accelerate the first build (UI + backend + database) while staying aligned with the architecture described above, a vibe-coding approach can be practical.
For example, Koder.ai lets teams create web applications through a chat-driven workflow while still producing a real codebase (React on the frontend, Go + PostgreSQL on the backend). That can be a good fit for compliance apps where you need:
The key is to treat the compliance requirements (event catalog, retention rules, approvals, and exports) as explicit acceptance criteria—regardless of how quickly you generate the first implementation.
Start with a plain-language statement like: “We need to show who did what, when, why, and under whose authority—and retrieve proof quickly.”
Then turn that into user stories per role (admins, control owners, end users, auditors) and a short v1 scope: roles + core workflows + audit trail + basic reporting.
A practical v1 usually includes:
Defer advanced dashboards and broad integrations until auditors and control owners confirm the fundamentals work.
Create a mapping table that converts abstract controls into buildable requirements:
Do this per in-scope product, environment, and data type so you don’t build controls for systems auditors won’t examine.
Model a small set of core entities and make relationships explicit:
Use stable human-readable IDs (e.g., CTRL-AC-001) and version policy/control definitions so old evidence stays tied to the requirement that existed at the time.
Define an “audit event” schema and keep it consistent:
Treat audit logs as immutable:
If something needs “correction,” write a new event that explains it rather than changing history.
Start with RBAC and least privilege (e.g., Viewer, Contributor, Control Owner, Approver, Admin). Then enforce scope:
Make separation of duties a code rule, not a guideline:
Treat role/scope changes and exports as high-priority audit events, and use step-up auth for sensitive actions.
Define retention by record type and store the applied policy with each record so it’s auditable later.
Common needs:
Add legal hold to override purges, and log retention actions (archive/export/purge) with batch reports. For privacy, decide when to delete vs. redact while keeping integrity (e.g., retain the audit event but redact personal fields).
Build investigation-style search and a small set of “audit questions” reports:
For exports (CSV/PDF), log:
Include an “as-of” timestamp and stable sorting so exports are reproducible.
Test audit readiness as a product requirement:
Operationally, treat deployments/config changes as auditable events, keep environments separated, and maintain runbooks (e.g., /docs/incident-response, /docs/audit-readiness) that show how you preserve integrity during incidents.
Standardize event types (auth, permission changes, workflow approvals, CRUD of key records) and capture before/after values with safe redaction.