Sep 03, 2025·8 min
How to Build a Web App to Manage Permissions Across Products
Learn how to design and build a web app that centralizes roles, groups, and permissions across multiple products, with audits, SSO, and safe rollout.
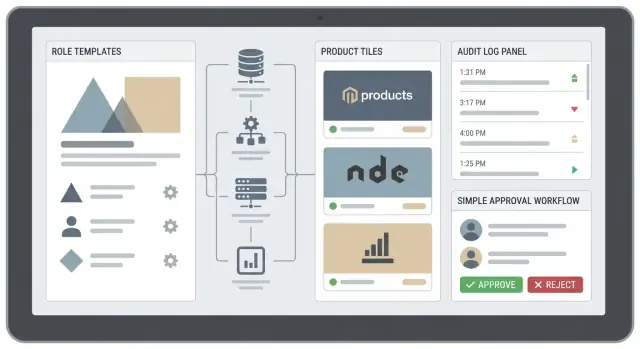
Learn how to design and build a web app that centralizes roles, groups, and permissions across multiple products, with audits, SSO, and safe rollout.

When people say they need to manage permissions across “multiple products,” they usually mean one of three things:
In all cases, the root issue is the same: access decisions are being made in too many places, with too many conflicting definitions of roles like “Admin,” “Manager,” or “Read-only.”
Teams typically feel the breakage before they can clearly name it.
Inconsistent roles and policies. One product’s “Editor” can delete records; another’s can’t. Users over-request access because they don’t know what they’ll need.
Manual provisioning and deprovisioning. Access changes happen through ad-hoc Slack messages, spreadsheets, or ticket queues. Offboarding is especially risky: users lose access in one tool but keep it in another.
Unclear ownership. Nobody knows who can approve access, who should review it, or who is accountable when a permission mistake causes an incident.
A good permissions management web app isn’t just a control panel—it’s a system that creates clarity.
Central admin with consistent definitions. Roles are understandable, reusable, and map cleanly across products (or at least make differences explicit).
Self-service with guardrails. Users can request access without hunting down the right person, while sensitive permissions still require approvals.
Approval flows and accountability. Every change has an owner: who requested it, who approved it, and why.
Auditability by default. You can answer “who had access to what, when?” without stitching together logs from five systems.
Track outcomes that align with speed and safety:
If you can make access changes faster and more predictable, you’re on the right path.
Before you design roles or pick a tech stack, get clear on what your permissions app must cover on day one—and what it explicitly won’t. A tight scope prevents you from rebuilding everything halfway through.
Start with a short list (often 1–3 products) and write down how each one currently expresses access:
is_admin flags?If two products have fundamentally different models, note that early—you may need a translation layer rather than forcing them into a single shape immediately.
Your permission system must handle more than “end users.” Define at least:
Capture edge cases: contractors, shared inbox accounts, and users who belong to multiple organizations.
List actions that matter to the business and users. Common categories include:
Write them as verbs tied to objects (e.g., “edit workspace settings”), not vague labels.
Clarify where identities and attributes originate:
For each source, decide what your permissions app will own vs. mirror, and how conflicts are resolved.
The first big decision is where authorization “lives.” This choice shapes your integration effort, your admin experience, and how safely you can evolve permissions over time.
With a centralized model, a dedicated authorization service evaluates access for all products. Products call it (or validate centrally-issued decisions) before allowing actions.
This is attractive when you need consistent policy behavior, cross-product roles, and a single place to audit changes. The main cost is integration: every product must depend on the shared service’s availability, latency, and decision format.
In a federated model, each product implements and evaluates its own permissions. Your “manager app” primarily handles assignment workflows and then syncs the result to each product.
This maximizes product autonomy and reduces shared runtime dependencies. The downside is drift: names, semantics, and edge cases can diverge, making cross-product administration harder and reporting less reliable.
A practical middle path is to treat the permission manager as a control plane (a single admin console), while products remain enforcement points.
You maintain a shared permission catalog for concepts that must match across products (e.g., “Billing Admin,” “Read Reports”), plus room for product-specific permissions where teams need flexibility. Products pull or receive updates (roles, grants, group mappings) and enforce locally.
If you expect frequent product growth, hybrid is often the best starting point: it delivers a single admin console experience without forcing every product onto the same runtime authorization engine on day one.
A permissions system succeeds or fails on its data model. Start simple with RBAC (role-based access control) so it’s easy to explain, administer, and audit. Then add attributes (ABAC) only where RBAC becomes too blunt.
At minimum, model these concepts explicitly:
project.read, project.write, billing.manage).A practical pattern is: role assignments bind a principal (user or group) to a role within a scope (product-wide, resource-level, or both).
Define roles per product so each product’s vocabulary stays clear (e.g., “Analyst” in Product A isn’t forced to match “Analyst” in Product B).
Then add role templates: standardized roles that can be reused across tenants, environments, or customer accounts. On top of that, create bundles for common job functions across multiple products (e.g., “Support Agent bundle” = roles in Product A + Product B + Product C). Bundles reduce admin effort without collapsing everything into one mega-role.
Make the default experience safe:
billing.manage, user.invite, and audit.export instead of hiding them under “admin.”Add ABAC when you need policy rules like “can view tickets only for their region” or “can deploy only to staging.” Use attributes for constraints (region, environment, data classification), while keeping RBAC as the main way humans reason about access.
If you want a deeper guide to role naming and scoping conventions, link your internal docs or a reference page like /docs/authorization-model.
Your permissions app sits between people, products, and policies—so you need a clear plan for how every request identifies who is acting, what product is asking, and which permissions should be applied.
Treat each product (and environment) as a client with its own identity:
Whichever you choose, log the product identity on every authorization/audit event so you can answer “which system requested this?” later.
Support two entry points:
For sessions, use short-lived access tokens plus a server-side session or refresh token with rotation. Keep logout and session revocation predictable (especially for admins).
Two common patterns:
A practical hybrid: JWT contains identity + tenant + roles, and products call an endpoint for fine-grained permissions when needed.
Don’t reuse user tokens for background jobs. Create service accounts with explicit scopes (least privilege), issue client-credential tokens, and keep them separate in audit logs from human actions.
A permissions app only works if every product can ask the same questions and get consistent answers. The goal is to define a small set of stable APIs that each product integrates once, then reuses as your portfolio grows.
Keep the core endpoints focused on the few operations every product needs:
Avoid product-specific logic in these endpoints. Instead, standardize on a shared vocabulary: subject (user/service), action, resource, scope (tenant/org/project), and context (attributes you may use later).
Most teams end up using a combination:
POST /authz/check (or uses a local SDK) on each sensitive request.A practical rule: make the centralized check the source of truth for high-risk actions, and use replicated data for UX (menus, feature flags, “you have access” badges) where occasional staleness is acceptable.
When permissions change, don’t rely on every product polling.
Publish events like role.granted, role.revoked, membership.changed, and policy.updated to a queue or webhook system. Products can subscribe and update their local caches/read models.
Design events so they’re:
Access checks must be fast, but caching can create security bugs if invalidation is weak.
Common pattern:
If you use JWTs with embedded roles, keep token lifetimes short and pair them with server-side revocation strategies (or a “token version” claim) so revokes propagate quickly.
Permissions evolve as products add features. Plan for it:
/v1/authz/check) and event schemas.A small investment in compatibility prevents the permissions system from becoming the bottleneck for shipping new product capabilities.
A permissions system can be technically correct and still fail if admins can’t confidently answer: “Who has access to what, and why?” Your UX should reduce guesswork, prevent accidental over‑granting, and make common tasks fast.
Start with a small set of pages that cover 80% of daily operations:
On every role, include a plain‑language explainer: “What this role allows” plus concrete examples (“Can approve invoices up to $10k” is better than “invoice:write”). Link to deeper docs when needed (e.g., /help/roles).
Bulk tools save time but amplify errors, so make them safe by design:
Add guardrails like “dry run,” rate limits, and clear rollback instructions if an import goes wrong.
Many organizations need a lightweight process:
Request → Approve → Provision → Notify
Requests should capture business context (“needed for Q4 close”) and duration. Approvals should be role‑ and product‑aware (the right approver for the right thing). Provisioning should generate an audit entry and notify both requester and approver.
Use consistent naming, avoid acronyms in the UI, and include inline warnings (“This grants access to customer PII”). Ensure keyboard navigation, readable contrast, and clear empty states (“No roles assigned yet—add one to enable access”).
Auditing is the difference between “we think access is correct” and “we can prove it.” When your app manages permissions across products, every change must be traceable—especially role grants, policy edits, and admin actions.
At minimum, log who changed what, when, from where, and why:
Treat audit events as append-only. Don’t allow updates or deletes through application code; if corrections are needed, write a compensating event.
Define retention by risk and regulation: many teams keep “hot” searchable logs for 30–90 days and archive for 1–7 years. Make export easy: provide scheduled delivery (e.g., daily) and streaming options to SIEM tools. At minimum, support export to newline-delimited JSON and include stable IDs so consumers can de-duplicate.
Build simple detectors that flag:
Surface these in an “Admin activity” view and optionally send alerts.
Make reporting practical and exportable:
If you later add approval workflows, link audit events to the request ID so compliance reviews are fast and defensible.
A permissions management app is itself a high‑value target: one bad decision can grant broad access across every product. Treat the admin surface and authorization checks as “tier‑0” systems.
Start with least privilege and make escalation intentionally hard:
Common failure mode: a “role editor” can edit the admin role, then assign it to themselves.
Admin APIs should not be as reachable as end‑user APIs:
Common failure mode: a convenience endpoint (e.g., “grant all for support”) shipped to production without guardrails.
HttpOnly, Secure, SameSite, short session lifetimes, and CSRF protection for browser flows.Common failure mode: leaking service credentials that allow policy writes.
Authorization bugs are usually “missing deny” scenarios:
A permissions system is never “done” at launch—you earn trust by rolling it out safely. The goal is to prove access decisions are correct, support can resolve issues quickly, and you can roll back changes without breaking teams.
Start with a single product that has clear roles and active users. Map its current roles/groups into a small set of canonical roles in your new system, then build an adapter that translates “new permissions” into whatever the product enforces today (API scopes, feature toggles, database flags, etc.).
During the pilot, validate the full loop:
Define success metrics up front: reduced support tickets for access, no critical over-permission incidents, and time-to-revoke measured in minutes.
Legacy permissions are messy. Plan a translation step that converts existing groups, ad-hoc exceptions, and product-specific roles into the new model. Keep a mapping table so you can explain every migrated assignment.
Do a dry run in a staging environment, then migrate in waves (by organization, region, or customer tier). For tricky customers, migrate but keep “shadow mode” enabled so you can compare old vs. new decisions before enforcing.
Feature flags let you separate the “write path” from the “enforcement path.” Typical phases:
If something goes wrong, you can disable enforcement while keeping audit visibility.
Document runbooks for common incidents: user can’t access a product, user has too much access, admin made a mistake, and emergency revoke. Include who is on call, where to check logs, how to verify effective permissions, and how to perform a “break-glass” revoke that propagates quickly.
Once the pilot is stable, repeat the same playbook product-by-product. Each new product should feel like integration work—not a reinvention of your permission model.
You don’t need exotic technology to ship a solid permissions management app. Prioritize correctness, predictability, and operability—then optimize.
A common baseline:
Keep the authorization decision logic in one service/library to avoid products drifting in behavior.
If you’re trying to get an internal admin console and APIs in place quickly (especially for a pilot), platforms like Koder.ai can help you prototype and ship the web app faster via a chat-driven workflow. In practice, that can be useful for generating a React-based admin UI, a Go + PostgreSQL backend, and the scaffolding for audit logs and approvals—then iterating as requirements become clearer. (You still need rigorous review for authorization logic, but it can shorten the time from spec to working pilot.)
Permissions systems quickly accumulate work that shouldn’t block user requests:
Make jobs idempotent and retryable, and store job status per tenant for supportability.
At minimum, instrument:
Alert on spikes in deny-by-error (e.g., DB timeouts) and on p95/p99 latency for permission checks.
Before rollout, load test the permission-check endpoint with realistic patterns:
Track throughput, p95 latency, and Redis hit rate; verify performance degrades gracefully when the cache is cold.
Once your core permission model works, a few “enterprise” features can make the system dramatically easier to operate at scale—without changing how your products enforce access.
Single Sign‑On usually means SAML 2.0 (common with older enterprise IdPs) or OpenID Connect (OIDC) (common with modern app stacks). Either way, the key design decision is: what do you trust from the Identity Provider (IdP)?
A practical pattern is to accept identity and high-level group membership from the IdP, then map those groups to your internal role templates per tenant. For example, an IdP group like Acme-App-Admins maps to your role Workspace Admin in tenant acme. Keep this mapping explicit and editable by tenant admins, not hard-coded.
Avoid using IdP groups as direct permissions. Groups change for organizational reasons; your app’s roles should remain stable. Treat the IdP as a source of “who the user is” and “which org group they’re in,” not “what they can do in every product.”
SCIM lets customers automate account lifecycle: create users, deactivate users, and sync group membership from the IdP. This reduces manual invites and closes security gaps when employees leave.
Implementation tips:
Multi-tenant access control must enforce tenant isolation everywhere: identifiers in tokens, database row-level filters, cache keys, and audit logs.
Define clear admin boundaries: tenant admins can manage users and roles only within their tenant; platform admins can troubleshoot without granting themselves product access by default.
For deeper implementation guides and packaging options, see /blog. If you’re deciding which features belong in which plan, align them with /pricing.
Start by listing 1–3 products to integrate first and document, for each one:
If models differ a lot, plan for a translation layer rather than forcing a single model immediately.
Pick based on where you want policy decisions to be evaluated:
If you expect multiple products and frequent change, hybrid is usually the safest default.
A practical baseline is RBAC with explicit entities:
billing.manage)Then store as: so you can reason about “who has what, where.”
Treat RBAC as the human interface and introduce ABAC only for constraints RBAC can’t express cleanly.
Use ABAC for rules like:
Keep it maintainable by limiting attributes to a small set (region, environment, data classification) and documenting them, while roles remain the primary way admins assign access.
Avoid a single mega-role by layering:
This reduces admin work without hiding important differences between products’ permission semantics.
Design around two decision patterns:
A common hybrid: JWT carries identity + tenant + roles, and products call a check endpoint for high-risk or fine-grained actions. Keep token lifetimes short and have a revocation strategy for urgent removals.
Keep a small “stable core” that every product can implement:
POST /authz/check (hot path)Standardize the vocabulary: , , , (tenant/org/workspace), and optional (attributes). Avoid product-specific branching in the core APIs.
Use events so products don’t need to poll for changes. Publish changes like:
role.granted / role.revokedmembership.changedpolicy.updatedMake events , when possible, and either (a) self-describing enough to update local state or (b) paired with a “fetch current state” endpoint for reconciliation.
Include the screens and guardrails that reduce mistakes:
Add plain-language role explainers and warnings for sensitive access (e.g., PII, billing).
Log every sensitive change as append-only events with enough context to answer “who had access to what, when, and why?”
At minimum capture:
Support export (e.g., newline-delimited JSON), long-term retention, and stable IDs for de-duplication in SIEM tools.