May 26, 2025·8 min
Create a Web App for Contract Review and Version Control
Learn how to plan, design, and build a web app for legal contract review with version control, comments, approvals, audit trails, and secure access.
Learn how to plan, design, and build a web app for legal contract review with version control, comments, approvals, audit trails, and secure access.

Before you sketch screens or pick a tech stack, get specific about the problem you’re solving. “Contract review” can mean anything from cleaning up a one-page NDA to coordinating a complex multi-party agreement with strict approval rules. Clear use cases keep your product from turning into a generic document tool that no one fully trusts.
Start by naming the real roles involved and what each one needs to do—often under time pressure:
When you write these down, also capture constraints like “must work on mobile,” “external users shouldn’t see internal notes,” or “approvals must be captured before signature.”
Your MVP should support a tight loop of activities that happen repeatedly:
If a job requires jumping between email, shared drives, and chat threads to “finish,” it’s a strong candidate for your app.
A contract can have multiple “truths” depending on the stage. Define your version states up front so everyone has the same mental model:
This definition later drives permissions (who can edit), retention (what can be deleted), and reporting (what counts as “final”).
Pick metrics you can measure without guesswork. Examples:
These metrics guide tradeoffs later—like investing in better search, a clearer workflow, or stricter role-based access control.
An MVP for a contract review web app should do a few things extremely well: keep documents organized, make edits and feedback easy to follow, and move a contract from “draft” to “signed” with a clear audit trail. If you try to solve every legal edge case on day one, teams will still fall back to email.
Start with one primary journey: upload a contract, invite reviewers, capture changes and comments, then approve and finalize.
Key MVP features to include:
Defer heavy automation such as advanced clause playbooks, AI-assisted rewriting, complex integrations, and multi-step conditional routing. These are valuable, but only after your core collaboration loop is reliable.
Define measurable outcomes: reviewers can understand the latest version in seconds, approvals are traceable, and teams can locate any contract or key clause quickly—without email threads.
A contract review app lives or dies by how well it separates “what the contract is” from “how it changes over time.” A clean data model also makes permissions, search, and auditability much easier later.
Model the top level as Workspaces (or “Clients/Teams”), then Matters/Projects inside each workspace. Within a matter, support folders for familiar organization, plus tags for cross-cutting grouping (e.g., “NDA,” “Renewal,” “High Priority”).
For each Contract, store structured metadata that users can filter on without opening a file:
Keep metadata flexible by using a small set of fixed fields plus a “custom fields” table (key + type + value) per workspace.
Think in three layers:
This separation allows one contract to have many versions and many threads, without mixing “document history” with “conversation history.”
Create an AuditEvent log that records actions as append-only events: who did what, when, from where (optional IP/user agent), and on which entity (contract/version/comment/permission). Examples: “version_uploaded,” “comment_added,” “status_changed,” “permission_granted,” “export_generated.”
Store enough context to be defensible in disputes, but avoid duplicating entire documents in the audit log.
Add fields for retention policy at the workspace/matter level (e.g., retain 7 years after close). For audits or litigation, provide export primitives: export contract metadata, all versions, comment threads, and the audit trail as a single package. Designing these entities early saves painful migrations later.
Security in a contract review app is mostly about two things: controlling who can see each document, and controlling what they can do with it. Make these rules explicit early, because they will shape your database model, UI, and audit trail.
Start with simple, recognizable roles and map them to actions:
Define permissions at the action level (view, comment, edit, download, share, approve) so you can evolve roles later without rewriting the app.
Most legal teams work by matter/deal. Treat a “matter” as the primary security boundary: users are granted access to matters, and documents inherit that access.
For external guests (counterparties, outside counsel), use restricted accounts:
Even with access checks, prevent accidental leakage:
Support password login by default, but plan for stronger options:
Keep all permission decisions server-side, and log access/permission changes for later investigation.
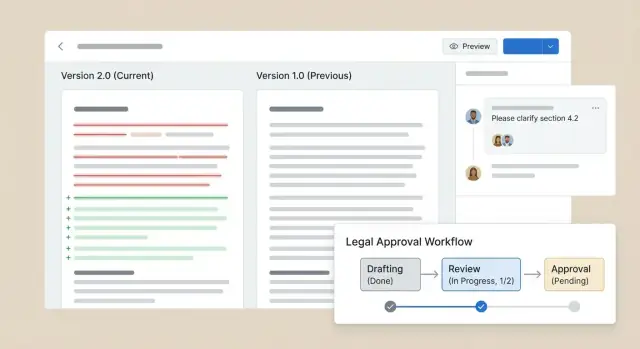
Redlining is the heart of a contract review web app: it’s where people understand what changed, who changed it, and whether they agree. The key is choosing a comparison approach that stays accurate while remaining readable for non-lawyers.
There are two common approaches:
DOCX-based diffs: You compare the underlying Word structure (runs, paragraphs, tables). This tends to preserve formatting and numbering, and matches how lawyers already work. The trade-off is complexity—DOCX is not “just text,” and small formatting tweaks can create noisy diffs.
Plain-text / clause-based diffs: You normalize content into clean text (or discrete clauses) and diff that. This can produce cleaner, more stable comparisons, especially if your product emphasizes clause library management. The trade-off is losing some layout fidelity (tables, headers, trackable formatting changes).
Many teams combine them: DOCX-aware parsing to extract stable text blocks, then diff those blocks.
Contracts rarely change linearly. Your document comparison diff should detect:
Reducing “diff noise” matters: normalize whitespace, ignore trivial formatting shifts, and preserve section numbering where you can.
Support comments attached to a range (start/end offsets) within a specific version, plus a fallback “rehydration” strategy if the text shifts (e.g., re-anchor via nearby context). Each comment should also feed the audit trail: author, timestamp, version, and resolution status.
Non-lawyers often need the headline, not the markup. Add a “Change Summary” panel that groups tracked changes by section and type (Added/Removed/Modified/Moved), with plain-language snippets and quick links that jump to the exact location.
A contract review web app succeeds or fails on how smoothly people can collaborate. The goal is to make it obvious who needs to do what, by when, and what changed, while preserving a defensible history.
Support inline comments anchored to a clause, sentence, or selected text. Treat comments as first-class objects: threads, @mentions, and file/version references.
Add clear controls to resolve and reopen threads. Resolved comments should stay discoverable for compliance, but collapse by default so the document stays readable.
Notifications matter, but they must be predictable. Prefer event-based rules (assigned to you, mentioned, your clause changed) and daily digests over constant pings. Let users tune preferences per contract.
Use lightweight assignments for sections or tasks (e.g., “Payment terms review”) and allow a checklist with organization-specific gates like “Legal approved” or “Security approved.” Keep checklists tied to a specific version so approvals remain meaningful even with tracked changes for contracts.
Define a small, understandable state machine: Draft → In Review → Approved → Executed (customizable per organization). Enforce gates: only certain roles can move a contract forward, and only when required checklist items are complete.
Pair this with role-based access control and immutable event logs (who changed status, who approved, when).
Add due dates at the contract and assignment level, with escalation rules (e.g., reminder 48 hours before, then on the due date). If a user is inactive, notify the assignee’s manager or fallback reviewer—without blasting the whole channel.
If you later add e-signature integration, align “Ready for signature” as a final gated status. See also /blog/contract-approval-workflow for deeper patterns.
Search is what turns a folder of contracts into a working system. It helps legal teams answer simple questions quickly (“Where is our limitation of liability clause?”) and supports operational questions (“Which vendor agreements expire next quarter?”).
Implement full-text search across both uploaded files and extracted text. For PDFs and Word docs, you’ll need a text extraction step (and ideally OCR for scanned PDFs) so searches don’t fail on image-based documents.
Keep results usable by highlighting matched terms and showing where they appear (page/section if possible). If your app supports versions, search should allow users to choose whether they’re searching the latest approved version, all versions, or a specific snapshot.
Full-text search is only half the story. Metadata makes contract work manageable at scale.
Common filters include:
From there, add saved views—pre-built or user-defined queries that behave like smart folders. For example: “Vendor MSAs expiring soon” or “NDAs missing signature.” Saved views should be shareable across a team and respect permissions, so a user never sees contracts they can’t access.
Clause management is where review becomes faster over time. Start by letting users tag clauses within a contract (e.g., “Termination,” “Payment,” “Liability”) and store those tagged snippets as structured entries:
A simple clause library enables reuse in new drafts and helps reviewers spot deviations. Pair it with search so a reviewer can find “indemnity” clauses across the library and across executed contracts.
Teams often need to act on groups of contracts: update metadata, assign an owner, change status, or export a list for reporting. Support bulk actions on search results, plus exports (CSV/XLSX) that include key fields and an audit-friendly timestamp. If you offer scheduled reports later, design exports now so they’re consistent and predictable.
Contracts live in other tools long before they reach your app. If file handling and integrations are awkward, reviewers will keep emailing attachments—and version control will quietly fall apart.
Start by supporting the two formats people actually send: DOCX and PDF. Your web app should accept uploads, normalize them, and render a fast in-browser preview.
A practical approach is to store the original file, then generate:
Be explicit about what happens when a user uploads a “scanned PDF” (image-only). If you plan OCR, surface it as a processing step so users understand why text search may be delayed.
Many contracts arrive through email. Consider a simple inbound email address (e.g., contracts@yourapp) that creates a new document or appends a new version when someone forwards a thread.
For external parties, prefer share links over attachments. A link-based flow can still preserve your version history: each upload via the link becomes a new version, with the sender captured as “external contributor” and a timestamp for your audit trail.
Focus on integrations that remove copying and re-uploading:
Expose a small set of reliable events and endpoints: contract.created, version.added, status.changed, signed.completed. This lets other systems synchronize status and files without brittle polling, while keeping your contract review web app as the authoritative timeline.
A contract review tool succeeds or fails on whether a busy reviewer can answer two questions quickly: what changed and what do you need from me. Design the UI around those moments, not around file management.
Make the default experience a simple, step-by-step review rather than a blank editor. A good flow is: open contract → see summary of changes and open items → review changes in order → leave comments/decisions → submit.
Use clear calls to action like “Accept change”, “Request edit”, “Resolve comment”, and “Send for approval”. Avoid jargon such as “commit” or “merge.”
For version comparison, provide a side-by-side view with:
When users click a change in the list, scroll to the exact location and briefly pulse-highlight it so they know what they’re looking at.
People trust what they can track. Use consistent labels such as v1, v2, plus optional human labels like “Vendor edits” or “Internal legal cleanup.” Display the version label everywhere: in the header, compare picker, and activity feed.
Support keyboard navigation (tab order, shortcuts for next/previous change), readable contrast, and scalable text. Keep the interface fast: render long contracts in chunks, preserve scroll position, and autosave comments without interrupting reading.
The best architecture for a contract review web app is usually the one your team can ship, secure, and maintain. For most products, start with a modular monolith (one deployable app, clearly separated modules) and only split into services when scale or team size truly requires it.
A typical setup looks like:
Most teams use React (or Vue) plus a document viewing layer (PDF viewer) and an editor surface for redlining. Real-time presence and updates can be done with WebSockets (or SSE) so reviewers see new comments and status changes without refresh.
Legal teams expect an audit trail for legal documents. Implement append-only audit logs for events like “uploaded,” “shared,” “commented,” “approved,” and “exported.” You can go “event sourcing-lite”: store immutable events, then build current state from them (or keep read models) for reliable history.
If your goal is to validate workflow and permissions quickly, a vibe-coding platform like Koder.ai can help you get a working prototype (React frontend + Go/PostgreSQL backend) from a chat-driven spec. It’s especially useful for scaffolding your contract data model, RBAC, audit events, and basic screens—then exporting the source code when you’re ready to harden diffing, OCR, and compliance-grade controls.
Contract review tools live and die by trust. Even if your product is “just” internal, treat security and governance as core product requirements—because contracts often contain pricing, personal data, and negotiation history.
Use TLS for all network traffic, and encrypt stored data at rest. Don’t stop at the document blobs: encrypt sensitive metadata too (party names, renewal dates, approver notes), because metadata is often easier to query and exfiltrate.
If you store files in object storage, enable server-side encryption and ensure encryption keys are managed centrally (and rotated). If you handle redlines as separate artifacts, apply the same controls to those derived files.
If you support multiple workspaces (customers, departments, subsidiaries), implement strict data segregation by tenant. This should be enforced at the data layer (not only in UI filters), with every query scoped to a tenant/workspace identifier.
Apply least privilege everywhere: default roles should have minimal access, and elevated actions (export, delete, share links, admin settings) should be explicit permissions. Tie this to your role-based access control model so audit logs are meaningful.
Backups are only useful if you can restore them. Define:
Document who can trigger restores and how you prevent accidental overwrites.
Maintain an audit trail for security and compliance: log authentication events, permission changes, document access/downloads, and key workflow actions. Review third-party vendors (storage, email, e-signature integration) for security posture, data location, and breach processes before going live.
A contract review web app lives or dies on trust: users need confidence that tracked changes for contracts are accurate, permissions are enforced, and every step in the contract approval workflow is recorded correctly. Treat testing and operations as core product features, not finishing touches.
Start with high-risk behaviors:
Contract files get big, and versions add up. Run load tests that simulate:
Track p95 latency for key actions: open document, generate diff, search, and export.
Instrument end-to-end monitoring for:
Create runbooks for common incidents (stuck diff job, failed conversion, degraded search). Add a lightweight status page at /status.
Ship with a controlled rollout: invite a small set of beta users, capture feedback inside the app, and iterate weekly. Keep releases small and reversible (feature flags help). Ongoing maintenance should include dependency patching, security reviews, periodic access audits, and regression tests for secure contract collaboration and e-signature integration.
Start with a tight, repeatable loop:
If users still have to “finish” the job in email or shared drives, your MVP is missing a core step.
Define the roles and their constraints early (legal, sales, procurement, external counsel). Then map each role to a small set of jobs-to-be-done:
This prevents building a generic document tool that lacks the workflow and trust features legal teams need.
Treat “version” as a set of explicit states with different rules:
Those definitions drive permissions (who can edit), retention (what can be deleted), and reporting (what counts as “final”).
Use a three-layer model:
This keeps document history and conversation history consistent, even as files change.
Make audit logging append-only and immutable. Log events such as:
version_uploadedcomment_addedstatus_changedpermission_grantedexport_generatedStore enough context to be defensible (who/what/when/where), but don’t duplicate full document contents inside the audit log.
Start simple with role-based access control (RBAC) and action-level permissions:
Make a matter/project the primary security boundary so documents inherit access rules, and keep all permission checks server-side with logging.
Use restricted guest accounts (or tightly-scoped share links) with:
Add safeguards like watermarking exports, download restrictions for sensitive matters, and careful separation of internal notes vs external-visible comments.
Pick a diff strategy aligned to what users expect:
In practice, many teams parse DOCX into stable blocks, normalize whitespace/formatting, and diff those blocks to reduce noise and improve readability.
Anchor comments to a specific version plus a text range (start/end) and store surrounding context for resilience. When text shifts, use a re-anchoring strategy (nearby context matching) rather than “floating” comments.
Also track resolution state (open/resolved/reopened) and include comment actions in the audit log for compliance.
Combine full-text search with structured metadata:
Add saved views (smart folders) that are shareable and permission-aware so users never see results they shouldn’t access.