Jun 14, 2025·8 min
Create a Web App to Manage Customer Consent & Preferences
Step-by-step guide to design, build, and deploy a consent & preference management web app with clear UX, audit logs, APIs, and strong security.
Step-by-step guide to design, build, and deploy a consent & preference management web app with clear UX, audit logs, APIs, and strong security.

Before you design screens or write code, get precise about what you’re building—and what you’re not. “Consent” and “preferences” sound similar, but they often have different legal and operational meanings. Getting these definitions right early prevents confusing UX and brittle integrations later.
Consent is a permission you must be able to prove later (who agreed, to what, when, and how). Examples include agreeing to receive marketing emails or allowing tracking cookies.
Preferences are user choices that shape experience or frequency (weekly vs. monthly updates, topics they care about). You should still store them reliably, but they’re usually not the same as a legal opt-in.
Write down what you’ll manage on day one:
A common pitfall is mixing marketing consent with transactional messages (like receipts or password resets). Keep them separate in your definitions, data model, and UI.
A consent management web app touches multiple teams:
Assign a clear owner for decisions, and define a lightweight process for updates when rules, vendors, or messaging change.
Pick a few measurable outcomes, such as fewer spam complaints, fewer unsubscribes caused by confusion, faster retrieval of GDPR consent records, fewer support tickets about subscription preferences, and reduced time-to-provide proof of consent when requested.
Translate privacy rules into practical product requirements. This section is a high-level orientation, not legal advice—use it to shape features, then confirm details with counsel.
At a functional level, a consent management web app usually needs to handle:
Your consent records should capture:
Define data retention policies for consent records and the audit log for consent (often retained longer than marketing data). Keep only what you need, protect it, and document retention periods. If you’re unsure, add a “needs legal decision” placeholder and link it to your internal policy docs (or /privacy if public).
Final policy decisions—especially what counts as “sale/share,” cookie categorization, and retention—should be reviewed with counsel.
A consent management web app lives or dies by its data model. If the schema can’t answer “who agreed to what, when, and how?”, you’ll struggle with compliance, customer support, and integrations.
Start with a few clear building blocks:
This separation keeps your preference center flexible while still producing clean GDPR consent records and CCPA opt-out signals.
Store the exact notice/policy version tied to each decision:
notice_id and notice_version (or a content hash)That way, when wording changes, older consents remain provable.
For each consent event, record evidence appropriate for your risk level:
People sign up twice. Model merges by linking multiple identifiers to one customer and recording a merge history.
Represent reversals explicitly:
status: granted / withdrawnwithdrawn_at and reason (user action, admin request)A preference center only works if people can quickly answer one question: “What will you send me, and how do I change it?” Aim for clarity over cleverness, and keep decisions reversible.
Make it easy to find and consistent wherever users interact with you:
Use the same wording and structure across all three so users don’t feel like they’ve landed somewhere unfamiliar.
Use short labels like “Product updates” or “Tips and how-tos,” and include a one-line description when needed. Avoid legalese.
Don’t use pre-checked boxes for consent where regulations or platform rules require affirmative action. If you must ask for multiple permissions, separate them clearly (e.g., marketing emails vs. SMS vs. sharing data with partners).
Let people opt in by topic and, if relevant, by channel (Email, SMS, Push). Then provide an easy global unsubscribe that is always visible.
A good pattern is:
For email signups, use double opt-in where needed: after the user selects preferences, send a confirmation email that activates the subscription only after they click the link. On the page, explain what happens next.
Ensure everything works with keyboard navigation, has clear focus states, sufficient contrast, and labels that screen readers can interpret (e.g., toggle labels that describe the outcome: “Receive weekly digest emails: On/Off”).
Your backend API is the source of truth for what a customer has agreed to and what they want to receive. A clean, predictable API also makes it easier to connect your preference center to email, SMS, and CRM tools without creating conflicting states.
Keep the surface area small and explicit. A typical set looks like:
GET /api/preferences (or GET /api/users/{id}/preferences for admin use)PUT /api/preferences for replacing the current set (clearer than partial updates)POST /api/consents/{type}/withdraw (separate from “update” so it’s never accidental)Make sure each consent type is named plainly (e.g., email_marketing, sms_marketing, data_sharing).
Browsers and integrations will retry requests. If a retry creates a second “unsubscribe” event, your audit trail gets messy. Support idempotency by accepting an Idempotency-Key header (or a request_id field) and storing the outcome so the same request produces the same result.
Reject anything you wouldn’t want to defend later:
granted, denied, withdrawn) and valid transitionsReturn predictable error shapes (e.g., code, message, field_errors) and avoid leaking details. Rate-limit sensitive endpoints like consent withdrawal and account lookup to reduce abuse.
Publish an internal API reference with copy-paste requests and responses (for the frontend and integrations). Keep it versioned (e.g., /api/v1/...) so changes don’t break existing clients.
Security is part of consent: if someone can hijack an account or spoof a request, they can change preferences without permission. Start by protecting identity, then lock down every action that modifies consent.
Use an approach that fits your audience and risk level:
Also add protections against account takeover: rate-limit login attempts, notify users of sensitive changes, and consider step-up verification before changing high-impact settings (e.g., marketing opt-in across all channels).
Treat the UI as untrusted. Your backend must verify:
Harden browser-facing endpoints with CSRF protection for cookie-based sessions, strict CORS rules (allow only your origins), and explicit checks on IDs to prevent horizontal privilege escalation.
Encrypt data in transit (HTTPS) and at rest. Collect the smallest set of fields needed to operate your preference center—often you can avoid storing raw identifiers by using internal IDs or hashed lookup keys. Set and enforce data retention policies for old logs and inactive accounts.
Audit logging is essential, but keep logs safe: don’t store full session tokens, magic-link tokens, or unnecessary personal data. For public-facing subscription forms, add CAPTCHA or throttling to reduce bot sign-ups and preference-tampering attempts.
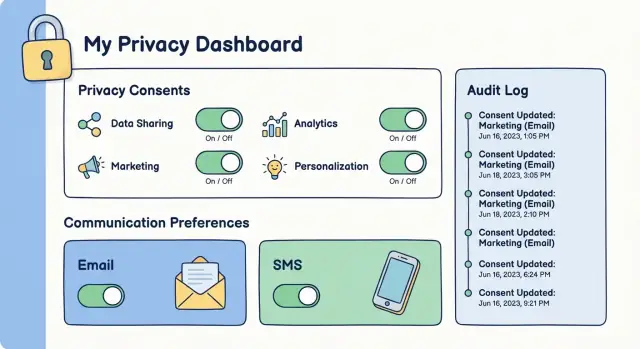
Audit logs are your receipt that a person gave (or withdrew) permission. They’re also how you explain what happened during a complaint, a regulator inquiry, or an internal incident review.
Every consent or preference update should produce an append-only audit event that captures:
This level of detail lets you reconstruct the full history—not just the latest state.
Operational logs (debug, performance, errors) rotate quickly and are easy to filter or drop. Audit logs should be treated as evidence:
An audit trail is only helpful if you can retrieve it. Provide searchable views by user ID, email, event type, date range, and actor. Also support export (CSV/JSON) for investigations—while keeping exports watermarked and traceable.
Audit data often includes identifiers and sensitive context. Define strict access controls:
Done well, audit logs turn consent management from “we think we did the right thing” into “here is the proof.”
Your consent management web app only works if every downstream system (email, SMS, CRM, support tools) reliably respects the latest customer choices. Integration is less about “connecting APIs” and more about ensuring preferences don’t drift over time.
Treat preference changes as events you can replay. Keep the payload consistent so every tool can understand it. A practical minimum is:
This structure helps build proof of consent while keeping integrations straightforward.
When a user updates your preference center, push the change immediately to your email/SMS providers and your CRM. For providers that don’t support your exact taxonomy, map your internal topics to their list/segment model and document the mapping.
Decide which system is the source of truth. Typically, it should be your consent API, with tools like ESPs and CRMs acting as caches.
Operational details matter:
Even with webhooks, systems drift (failed requests, manual edits, outages). Run a daily reconciliation job that compares your consent records to provider states and fixes discrepancies, while writing an audit entry for any automated correction.
Your consent app isn’t finished until it can handle real customer requests safely: “Show me what you have,” “Delete me,” and “Fix that.” These are core expectations under GDPR (access/rectification/erasure) and align with CCPA-style rights (including opt-out and deletion).
Provide a self-serve export that’s easy to understand and easy to deliver to support if the user can’t access their account.
Include in the export:
Keep the format portable (CSV/JSON) and name it clearly, like “Consent history export.”
When a user asks to delete, you often still need limited records for legal compliance or to prevent re-contact. Implement two paths:
Pair this with data retention policies so evidence isn’t kept forever.
Build admin tools for support tickets: search by user, view current preferences, and submit changes. Require a clear identity verification step (email challenge, existing-session check, or documented manual verification) before any export, deletion, or edit.
High-risk actions should use an approval workflow (two-person review or role-based approval). Log every action and approval in an audit trail so you can answer “who changed what, when, and why.”
Testing a consent management web app isn’t just “does the toggle move?” It’s proving that every downstream action (emails, SMS, exports, audience syncs) respects the latest customer choice, including under stress and edge cases.
Start with automated tests around your highest-risk rules—especially anything that could trigger unwanted outreach:
A helpful pattern is to test “given consent state X, system action Y is allowed/blocked,” using the same decision logic your sending systems call.
Consent changes happen at awkward times: two browser tabs open, a user clicks twice, a webhook arrives while an agent edits preferences.
The preference center is where mistakes are easiest:
Consent data is sensitive and often tied to identity:
End-to-end testing should include at least one “full journey” script: sign up → confirm (if required) → change preferences → verify sends are blocked/allowed → export proof of consent.
A consent app isn’t “set and forget.” People rely on it to reflect their choices accurately, every time. Reliability is mostly operational: how you deploy, how you observe failures, and how you recover when something goes wrong.
Use clear separation between dev, staging, and production. Staging should be production-like (same integrations, same configuration shape), but avoid copying real personal data. If you need realistic payloads for testing, use synthetic users and anonymized identifiers.
Consent history is a legal record, so plan database migrations carefully. Avoid destructive changes that rewrite or collapse historical rows. Prefer additive migrations (new columns/tables) and backfills that preserve the original event trail.
Before you ship a migration, verify:
Set up monitoring and alerts for:
Make alerts actionable: include the integration name, error code, and a sample request ID for quick debugging.
Have a rollback strategy for releases that accidentally flip defaults, break the preference center, or mis-handle opt-outs. Common patterns include feature flags, blue/green deploys, and quick “disable writes” switches that stop updates while keeping reads available.
If you’re building this system on a rapid iteration cycle, features like snapshots and rollback can be especially useful. For example, on Koder.ai you can prototype the React preference center and a Go + PostgreSQL consent API, then roll back safely if a change affects consent capture or audit logging.
Maintain lightweight documentation: release steps, alert meanings, on-call contacts, and incident checklists. A short runbook turns a stressful outage into a predictable procedure—and helps you prove you acted quickly and consistently.
Even a well-built consent management web app can fail in the details. These pitfalls show up late (often during legal review or after a customer complaint), so it’s worth designing against them early.
A common failure mode is letting downstream tools quietly overwrite choices—e.g., your ESP flips a user back to “subscribed” after an import, or a CRM workflow updates consent fields without context.
Avoid it by making your app the source of truth for consent and subscription preferences, and treating integrations as listeners. Prefer event-based updates (append-only events) over periodic syncs that can clobber state. Add explicit rules: who is allowed to change what, and from which system.
It’s tempting to log everything “just in case,” but collecting IP address, device fingerprints, or precise location can raise your compliance burden and risk.
Keep GDPR consent records focused on what you need to prove consent: user identifier, purpose, timestamp, policy/version, channel, and action. If you store IP/device data, document why, limit retention, and restrict access.
Pre-checked boxes, confusing toggles, bundled purposes (“marketing + partners + profiling”), or hard-to-find opt-outs can invalidate consent and harm trust.
Use clear labels, neutral design, and safe defaults. Make opt-out as easy as opt-in. If you use double opt-in, ensure the confirmation step is tied to the same purpose(s) and policy text.
Your policy text, purpose descriptions, or vendor list will change. If your system can’t track versions, you won’t know which users agreed to what.
Store a policy/version reference with each consent event. When changes are material, trigger re-consent and keep the old proof intact.
Building gives control, but it’s ongoing work (audits, edge cases, vendor changes). Buying can reduce time-to-value but may limit customization.
If you’re evaluating options, map requirements first, then compare total cost and operational effort. If you want to move quickly without giving up code ownership, a vibe-coding platform like Koder.ai can help you spin up a working preference center (React), backend services (Go), and a PostgreSQL schema with audit events—then export the source code when you’re ready to take it into your existing pipeline.
If you want a faster path, see /pricing.
Start by separating legal consent (permission you must prove later) from preferences (choices about topics/frequency). Then define day-one scope:
Finally, assign ownership (Product/Marketing/Legal) and pick measurable success metrics (fewer complaints, faster proof retrieval).
Consent is a legally meaningful permission you need to evidence: who agreed to what, when, and how.
Preferences are experience choices (topics, frequency) that should be stored reliably but usually don’t equal a legal opt-in.
Keep them separate in both definitions and UI so you don’t accidentally treat a preference toggle like a compliant consent record.
Most apps need, at minimum:
Treat this as product requirements input and confirm final interpretations with counsel.
Capture the “five W’s” of consent:
Model consent as events and preferences as current state, typically with:
Add merge history for duplicate signups and explicit withdrawal fields (withdrawn_at, reason) so reversals are unambiguous.
Store exactly what they saw when they decided:
notice_id + notice_version (or content hash)When wording changes, you can prove older consents without rewriting history, and you can trigger re-consent only when changes are material.
Common UX patterns that reduce confusion:
/preferences), in-app settings, embedded widgetAim for reversible decisions and consistent wording everywhere.
A practical core API set:
GET /api/preferences to read current statePUT /api/preferences to replace state explicitlyPOST /api/consents/{type}/withdraw for irreversible/legal withdrawal actionsMake updates (via /) and validate allowed states/transitions so you don’t accept changes you can’t defend later.
Treat preference changes as replayable events and define a consistent payload:
Make your consent API the source of truth, push changes immediately to ESP/SMS/CRM, and run a daily reconciliation job to detect and fix drift (with audit entries for automated corrections).
Use a layered approach:
Security failures can become consent failures if attackers can change choices.
This is what makes consent defensible later.
Idempotency-Keyrequest_id